I had a client that was dinged on a penetration test by having one communal password for the local administrator account on all machines. This is convenient for help desk, but is obviously very insecure. In the case of this client, the local admin password was commonly known, so they ran some sort of linuxsuperhacker utility from a central location with those credentials and found a laptop with a cached domain administrator account. This particular domain admin had chosen the option to store their password in clear text in RDCMan. Why the hell is that option even there? Anyways, from there it was over, and the first thing that would’ve prevented it all is securing the local admin password on each machine.
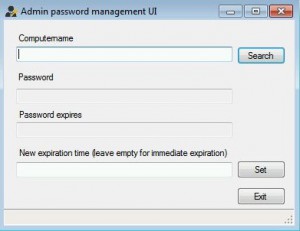
So, how do you do this? ::shrug:: Microsoft doesn’t have a solution. They just recommend disabling the account. But sometimes things get funky and you can’t log in with a domain account (cough.TrustRelationshipFailure.cough), and the help desk folks really need that account to make the world right again. Enter Jiri Formacek and his “Solution for management of built-in Administrator account’s password via GPO”. He saw the issue and he knew Active Directory schema extension, GPO, and apparently enough C# and C++ to make his dream a reality. If you’ve done any AD schema extension (say to store BitLocker Keys in AD), this isn’t scary, and it is very handy. Plus all settings are done via GPO and they’re nice and easy. But wait, there’s more – you can have the password expire itself and autogenerate a new one every XX amount of days.
This is a perfect fit, and something that should become an official Microsoft-supported solution. In the meantime, cheers to Jiri.